Updated on September 9, 2020 at 12:22 am
I’ve been reading up on threat modeling and specifically on IoT threat modeling and came across a great write-up at Microsoft.
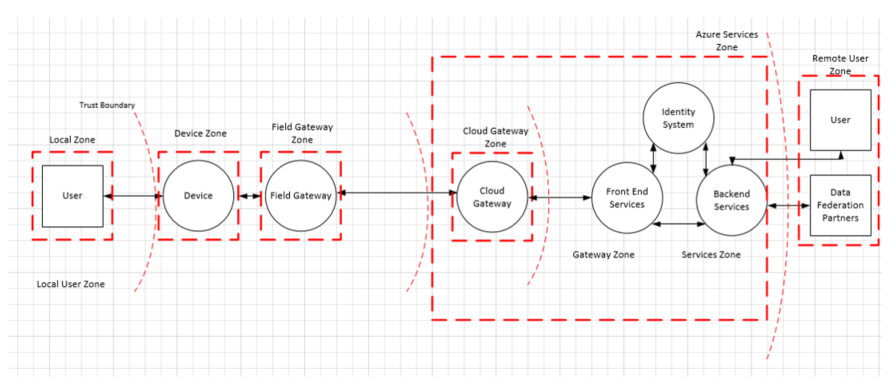
They divide the typical IoT architecture into four zones separated by trust boundaries:
- Device
- Field gateway
- Cloud gateway
- Services
And then the article goes through a threat identification exercise using STRIDE.
For example, under Tampering an attacker may be able to replace the firmware running on the device so you want to be able to ensure that only authorized firmware is allowed to run on the device.
The documentation is in relation to Microsoft’s Azure IoT services but still relevant for a great many IoT systems.
Have a look.